Post-Quantum Cryptography: Protecting Your Business from Quantum Threats

The Quantum Threat Is Real
Quantum computers are no longer science fiction. In 2025, these powerful machines can break the encryption that currently protects your business data, passwords, and secrets. This means your current security systems could become useless overnight.
What Is Post-Quantum Cryptography?
Post-quantum cryptography uses new mathematical methods that even quantum computers can't break. It's like upgrading from a regular lock to a quantum-proof vault.
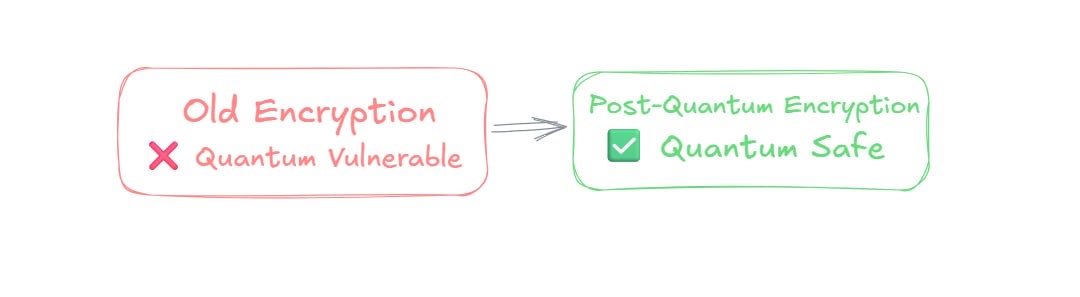
Current encryption vs. quantum-safe encryption
Why Your Current Security Is At Risk
Today's encryption relies on math problems that regular computers find hard to solve. Quantum computers can solve these problems easily:
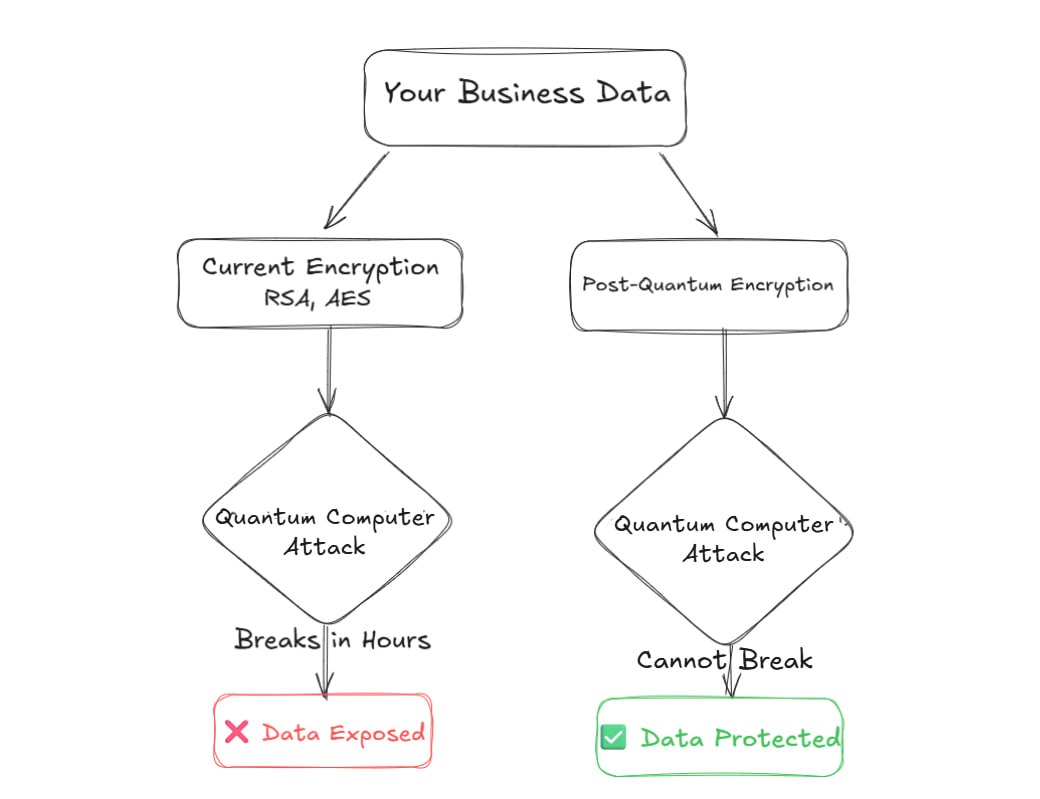
How quantum computers threaten current vs. future encryption
What Needs Protection Most
Your business has critical data that quantum computers could expose:
- API Keys & Passwords - Access to all your systems
- Customer Data - Personal and financial information
- Business Secrets - Proprietary information and trade secrets
- Financial Records - Transaction and accounting data
How Ennote Protects Your Secrets
Ennote's corporate secret manager uses advanced dual-layer encryption to provide maximum protection against both current and future quantum threats. While other companies are still planning, Ennote is already implementing military-grade security.
Ennote's Dual-Layer Security Architecture
Layer 1: Post-Quantum Key Generation
- Uses CRYSTALS-Kyber BCPQC (quantum-resistant algorithm) to generate ultra-secure private keys
- Protects against future quantum computer attacks
Layer 2: Military-Grade Data Encryption
- Encrypts your actual data with AES-256 encryption
- Provides immediate protection against all current threats
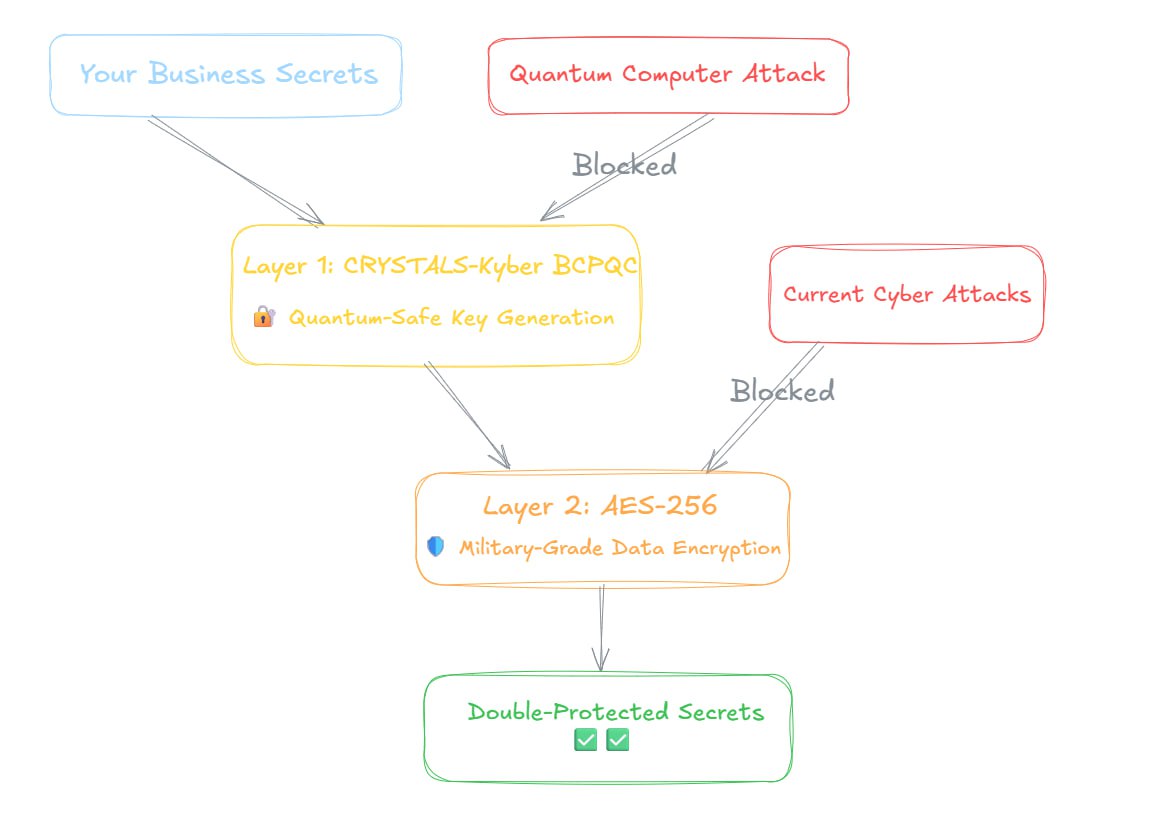
Ennote's dual-layer encryption protects against all threats
This double protection approach means your secrets are safe from today's hackers AND tomorrow's quantum computers. Most other solutions only protect against one or the other - Ennote protects against both.
Government Standards You Need to Know
The US government created new standards for quantum-safe encryption. Ennote implements these exact standards to keep your business compliant and secure:
- CRYSTALS-Kyber - Used by Ennote for quantum-safe key generation
- CRYSTALS-Dilithium - For digital signatures and authentication
- AES-256 - Military-grade encryption used by Ennote for data protection
By using CRYSTALS-Kyber BCPQC + AES-256, Ennote meets and exceeds all government security requirements.
Industry Impact
Different industries face different quantum risks:
Financial Services - Quantum computers could break banking encryption and expose transactions
Healthcare - Patient records need long-term protection that current encryption can't provide
Technology - Software companies must protect their code and customer data
Government - National security depends on quantum-resistant communication
Why Act Now
- Quantum computers are improving rapidly - The threat is growing every month
- Compliance requirements - Governments are starting to require quantum-safe security
- Competitive advantage - Early adopters will be more secure and trusted
Why Ennote Is Different
While other password managers and secret management tools are still using outdated encryption, Ennote is the only corporate secret manager that provides:
✅ Dual-layer protection (Post-quantum + Military-grade)
✅ CRYSTALS-Kyber BCPQC implementation (government standard)
✅ AES-256 encryption for immediate protection
✅ Future-proof security that works against quantum computers
✅ Zero-knowledge architecture - even Ennote can't see your secrets
This combination makes Ennote the most secure corporate secret manager available today.
"Will it slow down my systems?" Modern quantum-safe encryption has minimal performance impact with proper implementation.
"Is it expensive?" The cost of protection is much less than the cost of a quantum-powered data breach.
"Is it too complicated?" Solutions like Ennote handle the complexity for you with simple, managed services.
Start Your Quantum Protection Today
Don't wait for quantum computers to threaten your business. Take these immediate steps:
- Audit your current encryption - Know what you're protecting
- Prioritize critical systems - Focus on your most important data first
- Choose quantum-ready solutions - Partner with providers like Ennote who are already quantum-safe
- Plan your migration - Create a realistic timeline for full protection
The quantum revolution is happening now. Organizations that prepare today will stay secure and competitive tomorrow.
Ready to protect your business from quantum threats? Contact Ennote to see how our quantum-resistant corporate secret manager keeps your credentials safe.
